최근에 리눅스 머신 구매를 고려하던중 ODROID C2 와 같은 MCU인 Amlogic S905를 사용한 셑탑박스를 구매 하였다 (http://www.aliexpress.com/item/New-T95N-Mini-M8S-Pro-m8spro-Android-5-1-TV-Box-S905-Quad-Core-Bluetooth-Wifi/32670305568.html?spm=2114.13010608.0.97.YhH49H 무려 35$)
배송은 알리를 통해 1주일 걸렸고 상세 스펙은 다음과 같다.
CPU: Amlogic S905 quad-core cortex-A53 frequency 2.0G
GPU: Mali-450 5-Core GPU
RAM: 2GB DDR3
ROM: 8GB eMMC Flash 5.0 (Read 80MB/s above, Write 20MB/s above)
OS: Android 5.1
KODI: 16.0 Pre-installed and Play Well
Support 4kx2k H.265 Hardware Video Decode and 4Kx2K Output
Bluetooth 4.0
Ethernet: 10/100M, RJ-45
더 저렴한 제품(RAM 1G)이나 좀더 비싼제품 (Giga Ethernet)이 있었지만 그냥 대충 싼게….
ODROID C2와 비교했을때
C2는 아답터, EMMC, 리모컨, HDMI케이블, 케이스 별매 지만
(각 6,600, 21,600원, 4,800원, 4,400원 , 5,400원 VAT별도, tot :4만5천 정도)
USB 슬롯 4개, Gigabit ethernet, 좀더 거대한 방열판, GPOI 포트와 커뮤니티의 지원이 비교적(?) 활발한 장점을 가지고 있다(하지만 가격이 깡패다 C2살 돈이면 셋탑 두개사고 국밥한그릇 먹을수 있다)


받아보니 크기가 생각외로 매우 작았다.
어댑터가 EU 플러그라 그런지 조금 많이 헐겁다. 쓰기 굉장히 불안하게 생겼다 (왠지 쓰다보면 폭발할듯)
다행인지 USB포트를 통해 전원공급이 가능하였다(USB A male to USB A male 케이블 쓰면 된다)
더불어 샤오미 보조배터리 하나면 ODROID에서 6만원에 파는 UPS3을 대신할수있다. 가격도 싸고 용량도 크다
UART
켜보지도 않고 분해를 진행하였으며 목표했던 UART 단자를 찾았다(친절하게 프린팅 감사)


UART를 찍어보면 아래와 같은 로그가 나온다 (115200bd, 안드로이드 부팅로그 제외)
GXBB:BL1:08dafd:0a8993;FEAT:EDFC318C;POC:3;RCY:0;EMMC:0;READ:0;CHK:0;
TE: 270602
no sdio debug board detected
BL2 Built : 13:55:05, Jan 28 2016.
gxb g3625dd5 - xiaobo.gu@droid05
Board ID = 1
set vcck to 1100 mv
set vddee to 1000 mv
CPU clk: 1536MHz
DDR channel setting: DDR0 Rank0+1 diff
DDR0: 1024MB(auto) @ 912MHz(2T)-13
DDR1: 1024MB(auto) @ 912MHz(2T)-13
DataBus test pass!
AddrBus test pass!
Load fip header from eMMC, src: 0x0000c000, des: 0x01400000, size: 0x00004000
New fip structure!
Load bl30 from eMMC, src: 0x00010000, des: 0x01000000, size: 0x0000a9b0
Sending bl30...........................................OK.
Run bl30...
Load bl301 from eMMC, src: 0x0001c000, des: 0x01000000, size: 0x00001c20
Wait bl30...Done
Sending bl301........OK.
Run bl301...
Load bl31 from eMMC, src: 0x00020000, des: 0x10100000, size: 0x00012130
--- UART initialized after reboot ---
[Reset cause: unknown]
[Image: unknown, amlogic_v1.1.3054-53e549c 2016-03-31 20:40:25 xing.xu@droid05]
bl30: check_permit, count is 1
bl30: check_permit: ok!
chipid: ef be ad de d f0 aLoad bl33 from eMMC, src: 0x00034000, des: 0x01000000, size: 0x0009fd60
d ba ef be ad de not ES chip
efuse init ops = 13
efuse init hdcp = c, cf9=7
[0.401121 Inits done]
secure task start!
high task start!
low task start!
NOTICE: BL3-1: v1.0(debug):4c66217
NOTICE: BL3-1: Built : 17:13:36, Jan 28 2016
INFO: BL3-1: Initializing runtime services
WARNING: No OPTEE provided by BL2 boot loader
ERROR: Error initializing runtime service opteed_fast
INFO: BL3-1: Preparing for EL3 exit to normal world
INFO: BL3-1: Next image address = 0x1000000
INFO: BL3-1: Next image spsr = 0x3c9
U-Boot 2015.01-ga9e9562-dirty (May 26 2016 - 20:33:11)
DRAM: 2 GiB
Relocation Offset is: 76ed3000
register usb cfg[0][1] = 0000000077f62120
register usb cfg[0][2] = 0000000077f62140
register usb cfg[2][0] = 0000000077f62160
vpu detect type: 5
vpu clk_level = 7
set vpu clk: 666667000Hz, readback: 666660000Hz(0x300)
boot_device_flag : 1
Nand PHY Ver:1.01.001.0006 (c) 2013 Amlogic Inc.
init bus_cycle=6, bus_timing=8, system=5.0ns
reset failed
get_chip_type and ret:fffffffe
get_chip_type and ret:fffffffe
chip detect failed and ret:fffffffe
nandphy_init failed and ret=0xfffffff1
MMC: aml_priv->desc_buf = 0x0000000073ec3770
aml_priv->desc_buf = 0x0000000073ec5900
SDIO Port B: 0, SDIO Port C: 1
emmc/sd response timeout, cmd8, status=0x3ff2800
emmc/sd response timeout, cmd55, status=0x3ff2800
[mmc_init] mmc init success
mmc read lba=0x14000, blocks=0x400
Amlogic multi-dtb tool
Single dtb detected
start dts,buffer=0000000073ec7ff0,dt_addr=0000000073ec7ff0
parts: 11
00: logo 0000000002000000 1
01: recovery 0000000002000000 1
02: rsv 0000000000800000 1
03: tee 0000000000800000 1
04: crypt 0000000002000000 1
05: misc 0000000002000000 1
06: instaboot 0000000020000000 1
07: boot 0000000002000000 1
08: system 0000000040000000 1
09: cache 0000000020000000 2
10: data ffffffffffffffff 4
get_dtb_struct: Get emmc dtb OK!
overide_emmc_partition_table: overide cache
[mmc_get_partition_table] skip partition cache.
Partition table get from SPL is :
name offset size flag
===================================================================================
0: bootloader 0 400000 0
1: reserved 2400000 4000000 0
2: cache 6c00000 20000000 2
3: env 27400000 800000 0
4: logo 28400000 2000000 1
5: recovery 2ac00000 2000000 1
6: rsv 2d400000 800000 1
7: tee 2e400000 800000 1
8: crypt 2f400000 2000000 1
9: misc 31c00000 2000000 1
10: instaboot 34400000 20000000 1
11: boot 54c00000 2000000 1
12: system 57400000 40000000 1
13: data 97c00000 136500000 4
mmc read lba=0x12000, blocks=0x2
mmc read lba=0x12002, blocks=0x2
mmc_read_partition_tbl: mmc read partition OK!
eMMC/TSD partition table have been checked OK!
mmc env offset: 0x27400000
In: serial
Out: serial
Err: serial
[store]To run cmd[emmc dtb_read 0x1000000 0x40000]
read emmc dtb
Amlogic multi-dtb tool
Single dtb detected
Net: Meson_Ethernet
wipe_data=successful
wipe_cache=successful
upgrade_step=2
reboot_mode=cold_boot
hpd_state=0
[CANVAS]addr=0x3f800000 width=3840, height=2160
Not find '576cvbs' mapped VIC
amlkey_init() enter!
[EFUSE_MSG]keynum is 4
[KM]Error:f[key_manage_query_size]L504:key[usid] not programed yet
[KM]Error:f[key_manage_query_size]L504:key[deviceid] not programed yet
gpio: pin GPIOAO_3 (gpio 122) value is 1
saradc - saradc sub-system
Usage:
saradc saradc open <channel> - open a SARADC channel
saradc close - close the SARADC
saradc getval - get the value in current channel
saradc get_in_range <min> <max> - return 0 if current value in the range of current channel
Enter USB burn
Try connect time out 701, 700, 640
Hit any key to stop autoboot: 1 0
Booting...
Unknown command 'unifykey' - try 'help'
Unknown command 'unifykey' - try 'help'
[store]To run cmd[emmc dtb_read 0x1000000 0x40000]
read emmc dtb
Amlogic multi-dtb tool
Single dtb detected
ee_gate_off ...
## Booting Android Image at 0x01080000 ...
reloc_addr =73f481c0
copy done
Amlogic multi-dtb tool
Single dtb detected
load dtb from 0x1000000 ......
Uncompressing Kernel Image ... OK
kernel loaded at 0x01080000, end = 0x01f00fb8
Loading Ramdisk to 73c2c000, end 73ec1388 ... OK
Loading Device Tree to 000000001fff4000, end 000000001ffff0ab ... OK
signature:
fdt_instaboot: get header err
Starting kernel ...
uboot time: 2541079 us
부팅 도중 키입력을 하게되면 u-boot 쉘로 빠지게 된다.
baudrate=115200
bootargs=rootfstype=ramfs init=/init console=ttyS0,115200 no_console_suspend earlyprintk=aml-uart,0xc81004c0 ramoops.mem_address=0x20000000 ramoops.mem_size=0x
100000 ramoops.record_size=0x8000 ramoops.console_size=0x4000 androidboot.selinux=permissive logo=osd1,loaded,0x3f800000,576cvbs hdmimode=1080p60hz cvbsmode=57
6cvbs hdmitx= androidboot.firstboot=0 mac=c4:2f:ad:XX:XX:XX
androidboot.mac=c4:2f:ad:XX:XX:XX
bootcmd=run storeboot
bootdelay=1
bootmode_check=get_rebootmode; echo reboot_mode=${reboot_mode};if test ${reboot_mode} = factory_reset; then defenv_reserv aml_dt;setenv upgrade_step 2; save;fi;
bootup_offset=0x1080240
bootup_size=0x3f4c8
cmdline_keys=if keyman init 0x1234; then if keyman read usid ${loadaddr} str; then setenv bootargs ${bootargs} androidboot.serialno=${usid};fi;if keyman read mac ${loadaddr} str; then setenv bootargs ${bootargs} mac=${mac} androidboot.mac=${mac};fi;if keyman read deviceid ${loadaddr} str; then setenv bootargs ${bootargs} androidboot.deviceid=${deviceid};fi;fi;
cvbsmode=576cvbs
display_bpp=16
display_color_bg=0
display_color_fg=0xffff
display_color_index=16
display_height=576
display_layer=osd1
display_width=720
dtb_mem_addr=0x1000000
edid.crcvalue=0xe2070000
ethact=Meson_Ethernet
ethaddr=00:15:18:01:81:31
factory_reset_poweroff_protect=echo wipe_data=${wipe_data}; echo wipe_cache=${wipe_cache};if test ${wipe_data} = failed; then run init_display; run storeargs;if mmcinfo; then run recovery_from_sdcard;fi;if usb start 0; then run recovery_from_udisk;fi;run recovery_from_flash;fi; if test ${wipe_cache} = failed; then run init_display; run storeargs;if mmcinfo; then run recovery_from_sdcard;fi;if usb start 0; then run recovery_from_udisk;fi;run recovery_from_flash;fi;
fb_addr=0x3f800000
fb_height=1080
fb_width=1920
fdt_high=0x20000000
firstboot=0
gatewayip=10.18.9.1
hdmimode=1080p60hz
hostname=arm_gxbb
identifyWaitTime=750
init_display=hdmitx hpd;osd open;osd clear;vout output ${outputmode};imgread pic logo bootup $loadaddr;bmp display $bootup_offset;bmp scale
initargs=rootfstype=ramfs init=/init console=ttyS0,115200 no_console_suspend earlyprintk=aml-uart,0xc81004c0 ramoops.mem_address=0x20000000 ramoops.mem_size=0x100000 ramoops.record_size=0x8000 ramoops.console_size=0x4000 androidboot.selinux=permissive
ipaddr=10.18.9.97
irremote_update=if irkey 0xe31cfb04 0xb748fb04 2500000; then echo read irkey ok!; if itest ${irkey_value} == 0xe31cfb04; then run update;else if itest ${irkey_value} == 0xb748fb04; then run update;\fi;fi;fi;
loadaddr=1080000
mac=c4:2f:ad:xx:xx:xx
netmask=255.255.255.0
outputmode=576cvbs
preboot=run factory_reset_poweroff_protect;run upgrade_check;run bootmode_check;run init_display;run storeargs;run upgrade_key;run upgrade_sadckey;run switch_b
ootmode;
reboot_mode=cold_boot
recovery_from_flash=if imgread kernel recovery ${loadaddr}; then wipeisb; bootm ${loadaddr}; fi recovery_from_sdcard=if fatload mmc 0 ${loadaddr} aml_autoscript; then autoscr ${loadaddr}; fi;if fatload mmc 0 ${loadaddr} recovery.img; then if fatload mmc 0
${dtb_mem_addr} dtb.img; then echo sd dtb.img loaded; fi;wipeisb; bootm ${loadaddr};fi;
recovery_from_udisk=if fatload usb 0 ${loadaddr} aml_autoscript; then autoscr ${loadaddr}; fi;if fatload usb 0 ${loadaddr} recovery.img; then if fatload usb 0
${dtb_mem_addr} dtb.img; then echo udisk dtb.img loaded; fi;wipeisb; bootm ${loadaddr};fi;
sdc_burning=sdc_burn ${sdcburncfg}
sdcburncfg=aml_sdc_burn.ini
serverip=10.18.9.113
set=environment variables
stderr=serial
stdin=serial
stdout=serial
storeargs=setenv bootargs ${initargs} logo=${display_layer},loaded,${fb_addr},${outputmode} hdmimode=${hdmimode} cvbsmode=${cvbsmode} hdmitx=${cecconfig} andro
idboot.firstboot=${firstboot}; run cmdline_keys;
storeboot=echo Booting...; if unifykey get usid; then setenv bootargs ${bootargs} androidboot.serialno=${usid};fi;if unifykey get mac; then setenv bootargs ${
bootargs} mac=${ethaddr};fi;if imgread kernel boot ${loadaddr}; then store dtb read $dtb_mem_addr; bootm ${loadaddr}; fi;run update;
switch_bootmode=get_rebootmode;if test ${reboot_mode} = factory_reset; then run recovery_from_flash;else if test ${reboot_mode} = update; then run update;else
if test ${reboot_mode} = cold_boot; then run try_auto_burn; fi;fi;fi;
try_auto_burn=update 700 750;
update=run usb_burning; run sdc_burning; if mmcinfo; then run recovery_from_sdcard;fi;if usb start 0; then run recovery_from_udisk;fi;run recovery_from_flash;
upgrade_check=echo upgrade_step=${upgrade_step}; if itest ${upgrade_step} == 3; then run init_display; run storeargs; run update;else if itest ${upgrade_step}
== 1; then defenv_reserv; setenv upgrade_step 2; saveenv;fi;fi;
upgrade_key=if gpio input GPIOAO_3; then echo detect upgrade key; run update;fi;
upgrade_sadckey=saradc open 0; if saradc get_in_range 0 0x50; then sleep 1; if saradc get_in_range 0 0x50; then echo update by key...; run update; fi;fi;
upgrade_step=2
usb_burning=update 1000
wipe_cache=successful
wipe_data=successful
u-boot이 bootcmd 커맨드를 자동으로 실행되어 storeboot을 실행하게 되고 여기서 bootargs 를 설정하고, dtb를 읽고, 커널 읽고 bootm 을 통해 android를 부팅하는것을 확인할 수 있다.
안드로이드 부팅하면 root쉘이 자동으로 떠있다.
EMMC가 mmcblk0 으로 잡혀있고 mSD가 mmcblk1로 잡힌다
혹시 모를 상황에 대비해 전체 덤프 뜨고 c2용 armbian을 올렸….는데 부팅이 안된다. AHHHHH
Recovery / Debrick
인터넷 뒤적뒤적하니
http://forum.androidgadget.co.uk/showthread.php?tid=139
http://freaktab.com/forum/tv-player-support/amlogic-based-tv-players/s802/eny-acemax-ott/20156-help-ott-m8-bad-flash-recovery-using-shorted-nand-pins
이런 저런 신공으로 NAND에 호작질하여 복구한 것을 발견했는데….. 내가 구매한건 보드 레이아웃이 완전 다르다…….
데이터 시트를 보니 RCY가 0이 아니고, 2가 아닌경우 또는 모든 부팅 디바이스가 감지되지 않으면 USB Boot 으로 빠진다.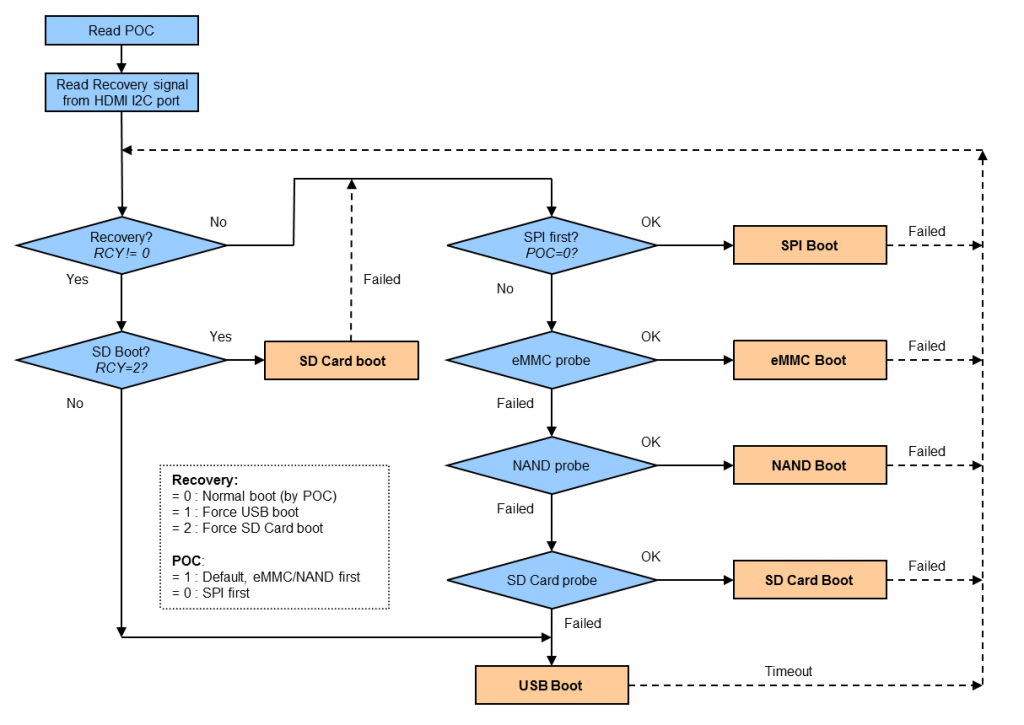 아마 NAND 쇼트 시키는거도 NAND 감지 못하게해서 USB Boot으로 빠지게 하는것으로 추정하고 eMMC 죽일 각오하고(데이터 시트에 따르면, 어차피 죽어도 SD 카드로는 부팅가능ㅋ) eMMC 주변의 핀들을 쇼트 시켰더니 컴퓨터에 idVendor=1b8e, idProduct=c003로 인식되었다.
아마 NAND 쇼트 시키는거도 NAND 감지 못하게해서 USB Boot으로 빠지게 하는것으로 추정하고 eMMC 죽일 각오하고(데이터 시트에 따르면, 어차피 죽어도 SD 카드로는 부팅가능ㅋ) eMMC 주변의 핀들을 쇼트 시켰더니 컴퓨터에 idVendor=1b8e, idProduct=c003로 인식되었다.

 NC랑 IO부분이랑 쇼트하면서 전원넣으면 된다. (사진은 180도 돌아가있다, NC는 Not Connected 인데 이상하게 GND에 연결되어있다)
NC랑 IO부분이랑 쇼트하면서 전원넣으면 된다. (사진은 180도 돌아가있다, NC는 Not Connected 인데 이상하게 GND에 연결되어있다) 불꽃놀이 이스터에그 보고싶으면 Vcc, Vss 쇼트하면 된다정상적인 입출력을 방해해서 NAND 또는 eMMC 통신을 막는것으로 추정된다
GXBB:BL1:08dafd:0a8993;FEAT:EDFC318C;POC:3;RCY:0;EMMC:0;READ:800;SD:800;USB:8;
usb 1-2: Manufacturer: Amlogic usb 1-2: USB disconnect, device number 12 usb 1-2: new high-speed USB device number 13 using xhci_hcd usb 1-2: New USB device found, idVendor=1b8e, idProduct=c003 usb 1-2: New USB device strings: Mfr=1, Product=2, SerialNumber=0 usb 1-2: Product: GX-CHIP
이후 윈도우에서 AMLOGIC_TOOL_setup_v2.0.5.15로 원본 펌웨어 플래싱하면된다
아래는 셀러를 통해 받은 오리지널 펌웨어 (AML BURN IMAGE 형식인듯?)
https://mega.nz/#F!5gMHBSyZ!MklQLG9LSnRzu8f5T9rqBw
이제 맘껏 죽여도 된다 (BL0을 건들수 있을진 모르겠지만 BL0 건들면 이방법도 답없을듯..)
ARMBIAN
이번엔 armbian을 eMMC가 아닌 SD카드에 구웠다. (dd명령어 이용)
두개의 파티션이 존재하며 파티션의 시작은 1049kB부터이다
Number Start End Size Type File system Flags 1 1049kB 68.2MB 67.1MB primary fat16 lba 2 68.2MB 1768MB 1700MB primary ext4
1번째 파티션에 부팅관련 이미지들, 2번째 파티션에는 Rootfs가 존재한다
이를 u-boot을 통해 부팅시키기 위해서 u-boot shell 에 접근하여 아래와 같이 타이핑(복붙안됨 아니 되는데 setenv 따로 fatload 따로 booti 따로 해줘야된다, 귀찮..)
setenv bootargs "root=/dev/mmcblk1p2 rootwait rootflags=data=writeback rw console=ttyS0,115200n8 fsck.repair=yes "
setenv loadaddr "0x1080000"
setenv dtb_loadaddr "0x1000000"
setenv initrd_loadaddr "0x13000000"
fatload mmc 0:1 ${initrd_loadaddr} uInitrd
fatload mmc 0:1 ${loadaddr} zImage
booti ${loadaddr} ${initrd_loadaddr} ${dtb_loadaddr}
우왕ㅋ 부팅 잘됨 ㅋ굳
이걸 영구히 eMMC에 넣어줄려니까 자꾸 BOOT 쪽이 깨져서 플래싱하는 경우가 생긴다
확인해보니 eMMC의 경우 파티션 영역이 부트영역에 저장되어있다 GPT, MBR 이런게 아니라 MPT(MMC Partition Table)라고
240:0000h: 4D 50 54 00 30 31 2E 30 30 2E 30 30 00 00 00 00 MPT.01.00.00.... 240:0010h: 0E 00 00 00 CA 70 F2 DE 62 6F 6F 74 6C 6F 61 64 ....ÊpòÞbootload 240:0020h: 65 72 00 00 00 00 00 00 00 00 40 00 00 00 00 00 er........@..... 240:0030h: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 240:0040h: 72 65 73 65 72 76 65 64 00 00 00 00 00 00 00 00 reserved........ 240:0050h: 00 00 00 04 00 00 00 00 00 00 40 02 00 00 00 00 ..........@..... 240:0060h: 00 00 00 00 00 00 00 00 63 61 63 68 65 00 00 00 ........cache... 240:0070h: 00 00 00 00 00 00 00 00 00 00 00 20 00 00 00 00 ........... .... 240:0080h: 00 00 C0 06 00 00 00 00 02 00 00 00 00 00 00 00 ..À............. 240:0090h: 65 6E 76 00 00 00 00 00 00 00 00 00 00 00 00 00 env............. 240:00A0h: 00 00 80 00 00 00 00 00 00 00 40 27 00 00 00 00 ..€.......@'.... 240:00B0h: 00 00 00 00 00 00 00 00 6C 6F 67 6F 00 00 00 00 ........logo.... 240:00C0h: 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 ................ 240:00D0h: 00 00 40 28 00 00 00 00 01 00 00 00 00 00 00 00 ..@(............ 240:00E0h: 72 65 63 6F 76 65 72 79 00 00 00 00 00 00 00 00 recovery........ 240:00F0h: 00 00 00 02 00 00 00 00 00 00 C0 2A 00 00 00 00 ..........À*.... 240:0100h: 01 00 00 00 00 00 00 00 72 73 76 00 00 00 00 00 ........rsv..... 240:0110h: 00 00 00 00 00 00 00 00 00 00 80 00 00 00 00 00 ..........€..... 240:0120h: 00 00 40 2D 00 00 00 00 01 00 00 00 00 00 00 00 ..@-............ 240:0130h: 74 65 65 00 00 00 00 00 00 00 00 00 00 00 00 00 tee............. 240:0140h: 00 00 80 00 00 00 00 00 00 00 40 2E 00 00 00 00 ..€.......@..... 240:0150h: 01 00 00 00 00 00 00 00 63 72 79 70 74 00 00 00 ........crypt... 240:0160h: 00 00 00 00 00 00 00 00 00 00 00 02 00 00 00 00 ................ 240:0170h: 00 00 40 2F 00 00 00 00 01 00 00 00 00 00 00 00 ..@/............ 240:0180h: 6D 69 73 63 00 00 00 00 00 00 00 00 00 00 00 00 misc............ 240:0190h: 00 00 00 02 00 00 00 00 00 00 C0 31 00 00 00 00 ..........À1.... 240:01A0h: 01 00 00 00 00 00 00 00 69 6E 73 74 61 62 6F 6F ........instaboo 240:01B0h: 74 00 00 00 00 00 00 00 00 00 00 20 00 00 00 00 t.......... .... 240:01C0h: 00 00 40 34 00 00 00 00 01 00 00 00 00 00 00 00 ..@4............ 240:01D0h: 62 6F 6F 74 00 00 00 00 00 00 00 00 00 00 00 00 boot............ 240:01E0h: 00 00 00 02 00 00 00 00 00 00 C0 54 00 00 00 00 ..........ÀT.... 240:01F0h: 01 00 00 00 00 00 00 00 73 79 73 74 65 6D 00 00 ........system.. 240:0200h: 00 00 00 00 00 00 00 00 00 00 00 40 00 00 00 00 ...........@.... 240:0210h: 00 00 40 57 00 00 00 00 01 00 00 00 00 00 00 00 ..@W............ 240:0220h: 64 61 74 61 00 00 00 00 00 00 00 00 00 00 00 00 data............ 240:0230h: 00 00 50 36 01 00 00 00 00 00 C0 97 00 00 00 00 ..P6......À—.... 240:0240h: 04 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................ 240:0250h: 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 ................
관련 코드는 AML u-boot source의 include/emmc_partitions.h, drivers/mmc/emmc_partitions.c 에 존재한다
적당히 저부분 수정 샥샥 해주고 부팅하니까 적용은 되는데 SPL 영역의 데이터와 다르다면서 다음 부팅에서는 다시 복원해버린다 -_-;
MPT부분 싹 날리고 부팅하니…… 안된다 부팅이 ….. u-boot 진입은 되는데 아예 파티션을 못찾는듯(SPL에서 복구하면 되잖아?)
U-boot Compile
linux-3.14-buildroot-pkg-201605-release-v1.2.pdf 9페이지 보면 툴체인 잘 구성하라고 나와있다
CodeSourcery.tar.gz
gnutools.tar.gz
gcc-linaro-aarch64-none-elf-4.8-2013.11_linux. tar
잘 받아서 잘 구성해주자.
$ tar zxf CodeSourcery.tar.gz -C /opt
$ tar zxf gnutools.tar.gz -C /opt
$ tar xf gcc-linaro-aarch64-none-elf-4.8-2013.11_linux.tar -C /opt
$ export PATH=$PATH: /opt/gnutools/arc2.3-p0/elf32-4.2.1/bin: /opt/CodeSourcery/Sourcery_G++_Lite/bin:/opt/CodeSourcery/Sourcery_G+ +_Lite/arm-none-eabi/bin:/opt/CodeSourcery/Sourcery_G+ +_Lite/arm-none-linux-gnueabi/bin:/opt/gcc-linaro-aarch64-none-elf-4.8-2013.11_li nux/bin/
u-boot 소스는 여기 uboot-2016-05-04-1fdf4683a5.tar.gz
make gxb_p200_v1_config 해주면 컴파일 잘된다.
잘 안되면 arch/arm/cpu/armv8/gxb/firmware/scp_task/Makefile 부터는 크로스 컴파일러를 CodeSourcery에 있는 컴파일러를 사용하게 지정해주면 된다.
mmcblk0에 fip/gxb/u-boot.bin을 올려주고 reboot을 하면 나의 uboot으로 부팅이 된다.
gxb_p200_v1#version U-Boot 2015.01 (Jul 21 2016 - 00:29:14) aarch64-none-elf-gcc (crosstool-NG linaro-1.13.1-4.9-2014.09 - Linaro GCC 4.9-2014.09) 4.9.2 20140904 (prerelease) GNU ld (crosstool-NG linaro-1.13.1-4.9-2014.09 - Linaro GCC 4.9-2014.09) 2.24.0.20140829 Linaro 2014.09
근데 여기서 다시 재부팅하면……….. 부팅이 안된다.
GXBB:BL1:08dafd:0a8993;FEAT:EDFC318C;POC:3;RCY:0;EMMC:0;READ:0;CHK:0; no sdio debug board detected TE: 146530 BL2 Built : 14:28:17, Apr 6 2016. gxb g61d9570 - xiaobo.gu@droid05 set vcck to 1100 mv set vddee to 1000 mv Board ID = 1 CPU clk: 1536MHz DDR chl: Rank0+1 same @ 912MHz DDR0: 1024MB(auto)-2T-13 DataBus test pass! AddrBus test pass! -s Load fip header from eMMC, src: 0x0000c000, des: 0x01400000, size: 0x00004000 New fip structure! Load bl30 from eMMC, src: 0x00010000, des: 0x01000000, size: 0x0000d460 Sending bl30......................................................OK. Run bl30... Load bl31 from eMMC, src: 0x00020000, des: 0x101b0000, size: 0x00013140 l30: check_permit, count is 1 bl30: check_permit: ok! efuse_pw_en: 0x3 ERROR! efuse license bits isLoad bl33 from eMMC, src: 0x00034000, des: 0x01000000, size: 0x000a1c00 disabled [Image: gxb_v1.1.3108-26b6c29 2016-04-27 18:35:06 xing.xu@droid05] efuse_setup() 223: OPS=0x13 bl30: check_permit, count is 1 bl30: check_permit: ok! chipid: ef be ad de d f0 ad ba ef be ad de not ES chip [0.257359 Inits done] secure task start! high task start! low task start!
low task start! 찍고 멈춰버린다. 로그를 보면 bl30이 제대로 올라가지 않은것으로 확인된다.(안올렸다!)
부트로더가지고 이것저것 하는거 지쳐서 그냥 microSD 카드에 OS넣고 부팅하기로 하였다.
uboot에서 아래의 명령어를 입력하면 microSD카드로 자동부팅하게된다
setenv sd_bootargs "root=/dev/mmcblk1p2 rootwait rootflags=data=writeback rw console=ttyS0,115200n8 fsck.repair=yes "
setenv loadaddr "0x1080000"
setenv dtb_mem_addr "0x1000000"
setenv initrd_loadaddr "0x13000000"
setenv sdboot "echo SD Booting.....; fatload mmc 0:1 ${initrd_loadaddr} uInitrd; fatload mmc 0:1 ${loadaddr} zImage; setenv bootargs ${sd_bootargs} ; booti ${loadaddr} ${initrd_loadaddr} ${dtb_mem_addr}"
setenv bootcmd "run sdboot"
gxb_p200_v1#env save
Saving Environment to aml-storage...
mmc env offset: 0x27400000
Writing to MMC(1)... done
gxb_p200_v1#reboot
근데 부팅할때마다 MAC이 바뀐다…
번외
bl2 Trusted Boot Firmware BL2
bl30 SCP Firmware BL3-0
bl301 SCP Firmware BL3-0-1
bl31 EL3 Runtime Firmware BL3-1
bl32 Secure Payload BL3-2 (Trusted OS)
bl33 Non-Trusted Firmware BL3-3
root@odroidc2:~# openssl speed md5 sha256 Doing md5 for 3s on 16 size blocks: 1766192 md5's in 3.00s Doing md5 for 3s on 64 size blocks: 1534685 md5's in 3.00s Doing md5 for 3s on 256 size blocks: 1041115 md5's in 3.00s Doing md5 for 3s on 1024 size blocks: 454482 md5's in 3.00s Doing md5 for 3s on 8192 size blocks: 72737 md5's in 2.99s Doing sha256 for 3s on 16 size blocks: 1804421 sha256's in 3.00s Doing sha256 for 3s on 64 size blocks: 1139236 sha256's in 3.00s Doing sha256 for 3s on 256 size blocks: 540779 sha256's in 3.00s Doing sha256 for 3s on 1024 size blocks: 174950 sha256's in 3.00s Doing sha256 for 3s on 8192 size blocks: 23918 sha256's in 2.99s OpenSSL 1.0.1t 3 May 2016 built on: Thu May 19 04:59:52 2016 options:bn(64,64) rc4(ptr,char) des(idx,cisc,16,int) aes(partial) blowfish(ptr) compiler: gcc -I. -I.. -I../include -fPIC -DOPENSSL_PIC -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -DL_ENDIAN -DTERMIO - g -O2 -fstack-protector-strong -Wformat -Werror=format-security -D_FORTIFY_SOURCE=2 -Wl,-z,relro -Wa,--noexecstack -Wall The 'numbers' are in 1000s of bytes per second processed. type 16 bytes 64 bytes 256 bytes 1024 bytes 8192 bytes md5 9419.69k 32739.95k 88841.81k 155129.86k 199284.78k sha256 9623.58k 24303.70k 46146.47k 59716.27k 65530.52k root@odroidc2:~# openssl speed rsa1024 Doing 1024 bit private rsa's for 10s: 3226 1024 bit private RSA's in 10.00s Doing 1024 bit public rsa's for 10s: 63910 1024 bit public RSA's in 9.99s OpenSSL 1.0.1t 3 May 2016 built on: Thu May 19 04:59:52 2016 options:bn(64,64) rc4(ptr,char) des(idx,cisc,16,int) aes(partial) blowfish(ptr) compiler: gcc -I. -I.. -I../include -fPIC -DOPENSSL_PIC -DOPENSSL_THREADS -D_REENTRANT -DDSO_DLFCN -DHAVE_DLFCN_H -DL_ENDIAN -DTERMIO - g -O2 -fstack-protector-strong -Wformat -Werror=format-security -D_FORTIFY_SOURCE=2 -Wl,-z,relro -Wa,--noexecstack -Wall sign verify sign/s verify/s rsa 1024 bits 0.003100s 0.000156s 322.6 6397.4

One thought on “Amlogic S905 Set-top box T95N M8S 2G/8G”