주방 240만원
싱크 2900mm, E0, 가스렌지 미포함, 수전내림
주방만 140, 신발장 개당 50, 2개 100만원 책정, 지인찬스
욕실, 타일 355만원
욕실 한칸, 비철거, 수전포함, 젠다이 작업 포함, 욕조철거, 파티션 안함, 기타선반 안함
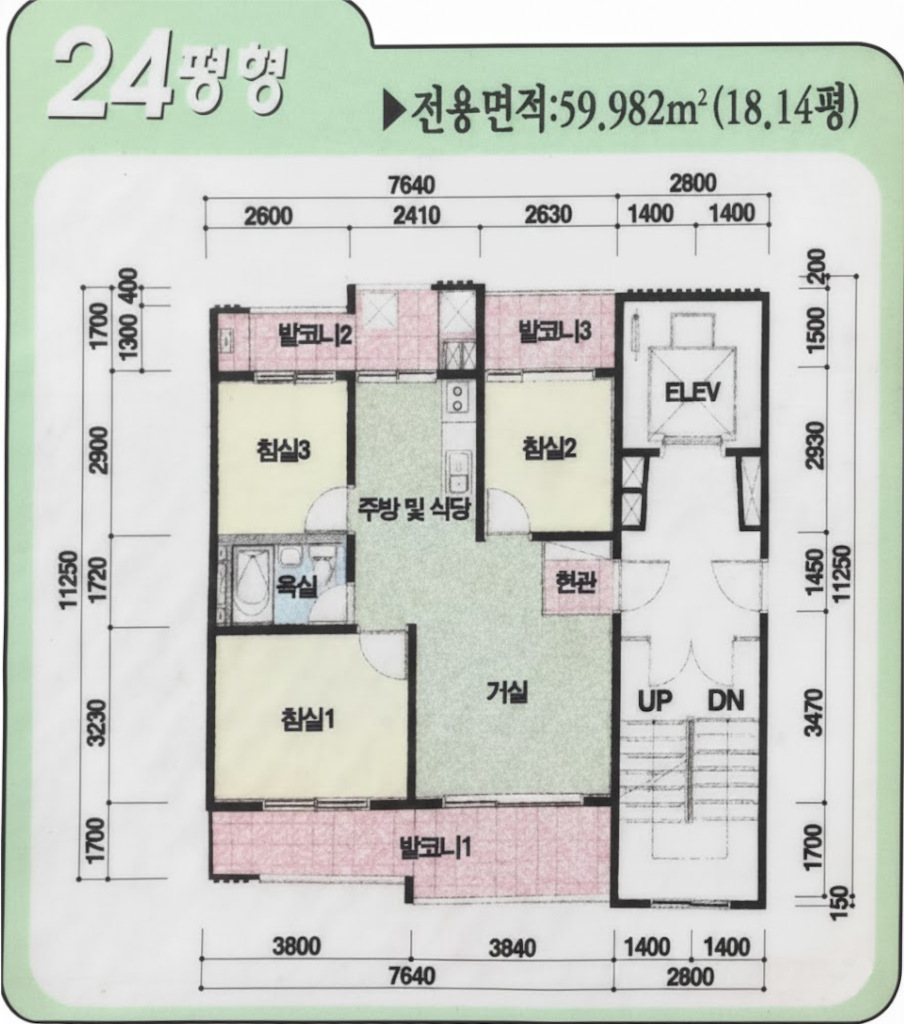
앞베란다, 뒷베란다 타일 + 걸레받이 (발코니3제외), 현관타일, 주방타일, 현관줄이기
샤시 540만원
영림프라임, 내측 5개 전부 2중창, 내측 로이유리 적용, 사다리차 포함
벽지 장판 몰딩 365만원
방4개, 주방, 거실,
장판 J플로어 2.4T, 벽지 개나리 실크, 4mm 몰딩, 걸레받이
페인트 (셀프진행)
베란다+방문 4개 페인트, 잡자재(퍼티, 롤러, 붓, 마스킹, 젯소, 바인더 등) 15만원
경첩, 문고리 (각 4개, 6만원)
전기자재 (셀프진행)
콘센트, 스위치, 전선, 분전함커버, 누전차단기 등 12만원
전등, T5, 매립등, 교체 여유분 한개씩 추가주문, 4만원
베란다 드레인, 드레인커버(셀프진행)
앞, 뒤 만원씩, 배송비포함 2.5만원정도 지출
드레인커버는 당근으로 3개 5천원에 구매 개이득
모두 철거, 폐기물 포함비용, 현금가